🧑💻Technology
Full Tech Deck will be released soon. Prepared to be impressed. In the mean time enjoy this high level summery.
Technical Architecture
The high-level architecture of our system consists of three primary components:
Polygon Network: This blockchain network hosts the game's smart contracts for rewards distribution, bid fee management, and other non-private aspects.
Secret Network: This blockchain network is used for the encryption of bids, ensuring a secure and private bidding process.
Custom Communication Layer: This layer facilitates secure data exchange between the Polygon and Secret Network contracts, ensuring seamless interaction between the two networks.
Core Features
Our technology offers several core features, including:
Privacy-Preserving Bidding: Users interact with the Secret Network to encrypt their bids directly from their browsers. These encrypted data are then submitted to the Polygon network for indexing and sync to the secret contract.
Secure Communication: Our custom communication layer ensures the secure exchange of encrypted bid data between the Polygon and Secret Network, maintaining the game's privacy and integrity.
Rewards Distribution: Rewards are distributed on the Polygon network, offering a seamless user experience.
Privacy and Security
Privacy and security are at the heart of our technology. We leverage Secret Network's encryption capabilities to enable users to submit encrypted bids without revealing their bid amounts. Additionally, our custom communication layer ensures secure data exchange between the Polygon and Secret Network components, protecting sensitive user information and maintaining game integrity.
Scalability and Interoperability
Our solution is built to scale to support many users and transactions without compromising performance. Using Polygon network's scalability features ensures the game can handle high demand with a minimum cost per transaction. Moreover, our custom communication layer enables seamless interaction between Polygon and Secret Network, demonstrating the interoperability of our solution with different blockchain networks.
Auction Flow
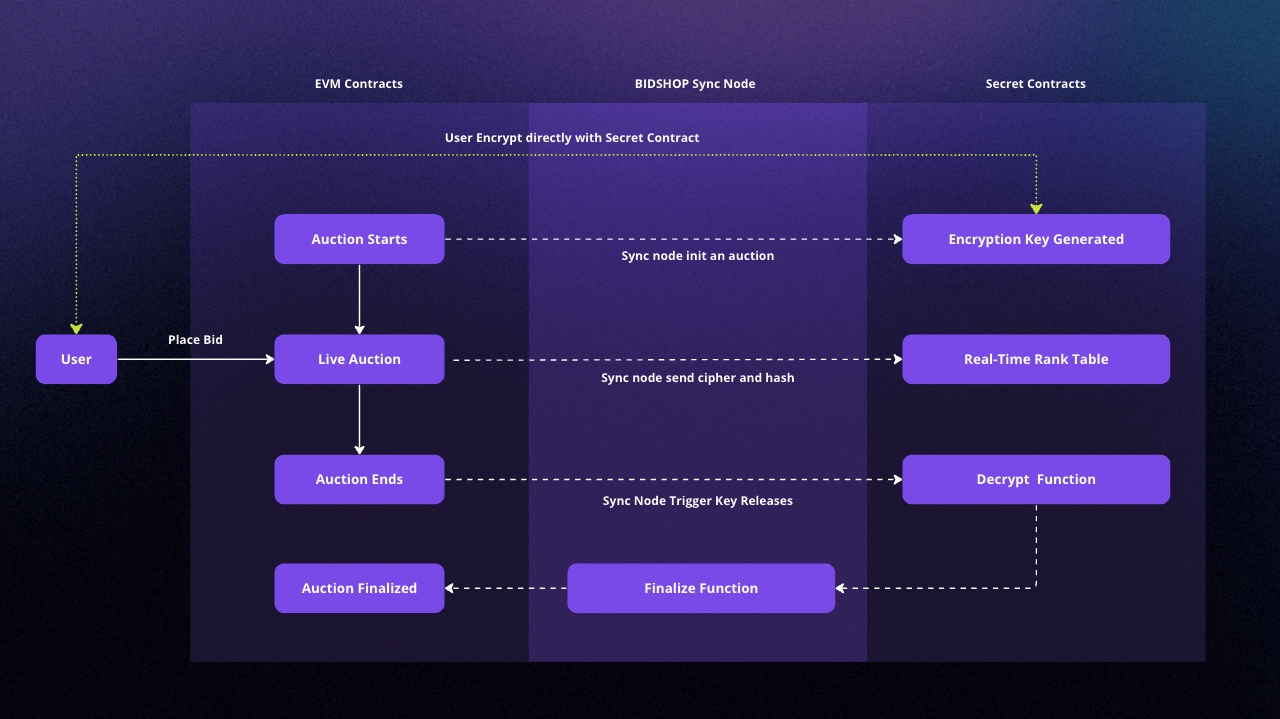
Our cross-chain auction game follows a well-defined sequence of steps to ensure secure, private, and fair gameplay. Below is the outline of the game's auction flow:
Encryption Key Generation: An encryption key is generated within the enclave of the Secret Network. This encryption function is available for all users to encrypt their bids but cannot be used to decrypt them.
Bid Encryption: Users place bids by encrypting their bid amounts directly against the encryption function with the secret contract. This process does not reveal the bid amounts to anyone, ensuring privacy.
Cipher and Hash Transaction: The encrypted bids (ciphers) and their corresponding hashes are submitted to the EVM contract hosted on the Polygon network.
Rank Table Generation: Our custom communication layer feeds the ciphers to the Secret Network, which generates a real-time rank table based on the encrypted bids.
Auction Ends: The auction concludes after a predetermined period. No new bids can be placed or processed after this point.
Key Release: Our custom communication layer releases the encryption key, allowing all parties to decrypt the bids. This process is facilitated only after the auction ends, ensuring fair gameplay.
Finalization: The custom communication layer feeds the decrypted bid amounts to the EVM contract on the Polygon network for finalization and reward distribution.
By following this sequence, our technology ensures a secure, private, and fair bidding environment that provides an engaging user experience while preserving the integrity of the game.
Encryption Algorithm
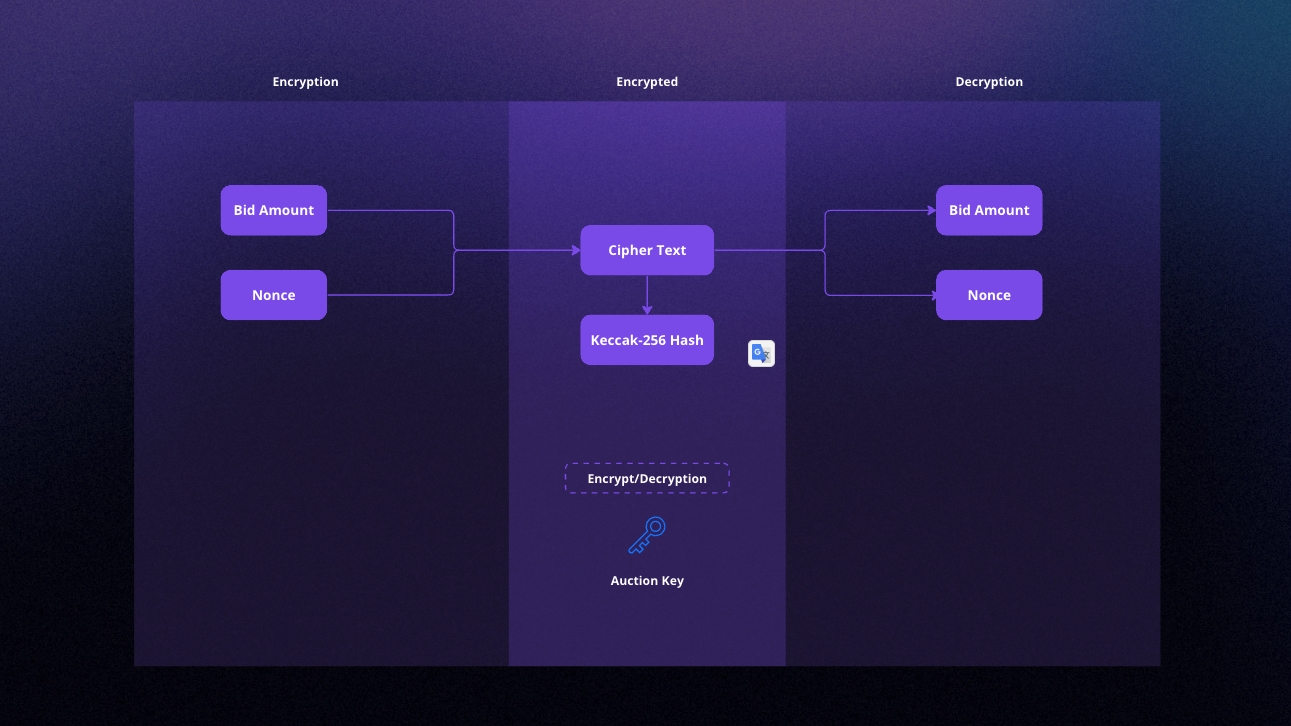
To ensure the highest security and privacy in our cross-chain auction game, we use the XChaCha20 encryption algorithm, and a random nonce is generated each time a user bids. This approach helps protect the confidentiality of bid amounts while maintaining the integrity of the game.
The auction key and nonce, used for encrypting bids with XChaCha20, are randomly created for every auction. Our custom communication layer can only reveal these values during the auction. Importantly, our smart contract on the Secret Network includes a time check condition that prevents the custom communication layer from revealing the bid amounts before the auction's end time. This mechanism ensures that the bid amounts remain private and secure throughout the auction process, and only the necessary information is revealed when required.
Why Secret Network
Privacy & Security: Secret Network is unique because it uses symmetric and asymmetric encryption protocols, ensuring robust security and privacy. For example, asymmetric cryptography achieves consensus and shares secrets between nodes and users. While symmetric cryptography is for input/output encryption with users of Secret Contracts and internal contract state encryption. This approach effectively maintains the confidentiality of users' bids until the end of the auction and protects sensitive information.
Advanced Encryption Protocols: The Secret Network uses the Elliptic-curve Diffie-Hellman (ECDH) key exchange mechanism between users and validators, alongside other cutting-edge encryption and key derivation, functions like HKDF-SHA256 and AES-128-SIV.
Fairness: Our game's fairness is achieved by the Secret Network's ability to enforce critical conditions in smart contracts, such as making the encryption key available only after the auction ends. As a result, this guarantees every participant an equal and fair chance of winning the auction.
Transparency: While preserving privacy, Secret Network provides the necessary transparency for our game. Users can verify the legitimacy of the auction process and our custom communication layer's reliability through our verification instructions.
Fairness and Verification of Auctions
Ensuring the fairness of an auction is integral to our technology. Below, we outline the mechanisms and steps involved in proving that an auction was conducted fairly:
Encryption Source Declaration: A secret contract is declared the encryption source for all auctions.
Key Allocation: Each auction is allocated a dedicated encryption key.
Hash Generation: Hashes are generated from a bid amount and a nonce. When the ciphers are revealed, the bid amount and nonce must match their corresponding hash.
The integrity of the custom communication layer can be verified retroactively. It can be exposed at any time if it is found to have provided false information.
The steps to verify a finalized round are as follows:
Fetch all fed bid hashes and ciphers of a round (e.g., with SubGraph).
Decrypt all the ciphers using the designated auction ID in the secret contract.
Fetch all the bid values from the EVM contract hosted on the Polygon network.
The decrypted bid amounts should match the amounts in the EVM contract, given that the nonce and bid amount from a cipher match. If a cipher of an auction is decryptable via its designated key, but the bid amount is not present in the EVM contract, the custom communication layer is proven guilty.
Additional checks for the legitimacy of the custom communication layer include:
Each auction should have the same number of bids on the EVM and Secret Network, excluding bids with invalid ciphers.
The release of the encryption key should always occur after the final block of the auction has been executed.
These mechanisms and verification steps ensure the fairness and reliability of our cross-chain auction game, providing users with confidence in the integrity of the process.
Last updated